Application Security Testing:
The SAST vs. DAST Crash Test
The digitization of business processes has turned applications into the lifeblood of businesses, driving innovation and enabling seamless interactions with customers and partners. We wouldn’t exaggerate if we say modern companies have transformed into software entities. However, with this increasing reliance on software comes a heightened risk of cyberattacks. Application security (AppSec) testing plays a crucial role in safeguarding these critical assets and protecting sensitive data from malicious exploitation.
AppSec testing encompasses a suite of methodologies designed to identify and remediate application vulnerabilities before attackers can exploit them. Driven by international standards for secure code development, such as PCI DSS 4.0 and ISO/IEC 27001, the most prominent automated approaches within AppSec testing are Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST). While both aim to secure applications, they differ in their execution and effectiveness.
Delving into the Dynamic vs. Static Testing Dichotomy
SAST, often called “white-box testing,” analyzes the application’s source code during development. It meticulously examines the code’s structure and syntax, looking for potential flaws like SQL injection, cross-site scripting (XSS), and insecure coding practices such as hardcoded credentials. SAST’s strength lies in its early detection capabilities, allowing developers to address vulnerabilities promptly and prevent them from propagating further.
On the other hand, DAST takes a more “black-box” approach, testing the application in its deployed environment. It simulates real-world attacks by sending various inputs and payloads to the application’s endpoints, observing how it responds, and identifying potential vulnerabilities. DAST detects vulnerabilities that only manifest during runtime, such as misconfigurations, insecure web services, and application logic issues.
Comparing the Pros and Cons of Each Approach
The question that many developers and clients ask is which testing method to choose. While the unpopular answer is “well, it depends,” giving a more accurate response requires understanding their advantages and drawbacks. Let’s examine them.
SAST offers several advantages:
- Early Identification: SAST detects vulnerabilities and indications of weaknesses early in the development cycle, enabling developers to address them promptly and prevent them from becoming more complex or resource-intensive to fix.
- Comprehensive Code Coverage: SAST can analyze the entire codebase, including complex logic and hidden vulnerabilities that may not be apparent during runtime testing.
- Third-Party and Legacy Code Handling: SAST can handle third-party and legacy code with minimal or no modifications. This is essential for businesses with hybrid environments, where legacy systems coexist with state-of-the-art ones like banks.
However, SAST also has some limitations:
- Source Code Requirement: SAST requires access to the application’s source code, which may not always be readily available, especially for third-party components.
- False Positives: SAST tools may generate false positives, requiring manual verification and investigation to eliminate false alarms.
- Limited Runtime Testing: SAST cannot detect vulnerabilities that only appear during runtime, such as misconfigurations or injection flaws arising from interactions with external systems.
DAST, in contrast, offers its own set of benefits:
- Real-World Testing: DAST tests the application in its actual environment, simulating real-world attack scenarios and identifying vulnerabilities that may not manifest during static analysis.
- Runtime Vulnerability Detection: DAST effectively detects vulnerabilities that only become apparent during runtime, such as misconfigurations and injection flaws.
- Source Code Independence: DAST does not require access to the application’s source code, making it suitable for testing third-party applications or components.
However, DAST also faces challenges:
- Limited Code Coverage: DAST may not detect vulnerabilities deep within the application’s logic or configuration, especially if they are not directly exposed to user input. When these vulnerabilities are identified, this is usually done “late” in the SDLC pipeline.
- Higher False Positives: DAST tools can generate a higher number of false positives compared to SAST, requiring more time and effort for manual investigation.
- Legacy and Obfuscated Code Limitations: DAST may not be as effective in testing legacy code or code that has been heavily obfuscated to prevent reverse engineering.
The following table provides a quick overview of the pros and cons of each AppSec testing method.
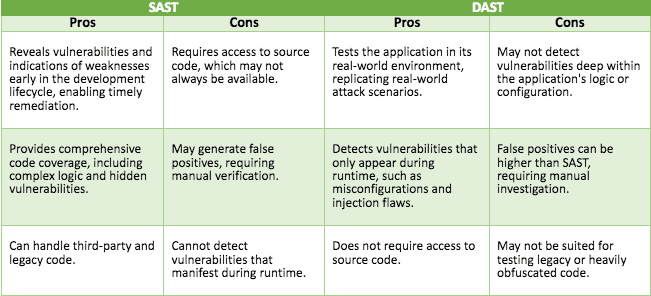
SAST
DAST
Pros
Reveals vulnerabilities and indications of weaknesses early in the development lifecycle, enabling timely remediation.
Cons
Requires access to source code, which may not always be available.
Pros
Tests the application in its real-world environment, replicating real-world attack scenarios.
Cons
May not detect vulnerabilities deep within the application’s logic or configuration.
Provides comprehensive code coverage, including complex logic and hidden vulnerabilities.
May generate false positives, requiring manual verification.
Detects vulnerabilities that only appear during runtime, such as misconfigurations and injection flaws.
False positives can be higher than SAST, requiring manual investigation.
Can handle third-party and legacy code.
Cannot detect vulnerabilities that manifest during runtime.
Does not require access to source code.
May not be suited for testing legacy or heavily obfuscated code.
Choosing the Right Testing Method: A Holistic Approach
Achieving comprehensive application security requires a balanced approach that leverages the strengths of both SAST and DAST. While SAST shines in early vulnerability detection and code coverage, DAST excels in runtime testing and real-world scenario simulation. By integrating both approaches, organizations can better understand their application’s security posture and address vulnerabilities throughout the development lifecycle.
Implementing a Successful DevSecOps Program
A phased approach, beginning with SAST, is recommended for applications with complex logic or sensitive data. Combining SAST with Software Composition Analysis (SCA), businesses can identify code and dependency vulnerabilities early in the development cycle before they become deeply embedded in the code. By addressing these vulnerabilities promptly, developers can prioritize their resolution by criticality and prevent them from propagating and becoming more challenging to fix.
DAST for Runtime Validation
DAST should be incorporated as the application progresses through testing and deployment to validate its security in its real-world environment. DAST simulates real-world attack scenarios, sending various inputs and payloads to the application’s endpoints. This allows for the identification of vulnerabilities that may not have been apparent during static analysis, such as misconfigurations or injection flaws. The mapping and correlation of DAST findings with the SAST ones provide an even better understanding of the vulnerabilities looming in the code under development.
Factors Influencing Testing Method Selection
The choice of which testing method to prioritize depends on several factors, including:
- Application Type: Applications with complex logic or sensitive data may benefit from a more SAST-focused approach, while applications with high runtime exposure may require greater emphasis on DAST.
- Development Stage: SAST is most effective early in the development cycle, while DAST is better suited for testing deployed applications.
- Risk Tolerance: Organizations with higher risk tolerance may prioritize DAST for its ability to identify runtime vulnerabilities, while those with lower risk tolerance may rely more heavily on SAST’s early detection capabilities.
A holistic application security strategy embraces both SAST and DAST, ensuring that applications are thoroughly tested throughout the development lifecycle. This comprehensive approach helps organizations identify and address vulnerabilities early, minimizing their impact on security and protecting sensitive data from malicious attacks.
The Experts’ Perspective
As software engineering and security experts, we focus on pre-emptive measures in secure coding, examining design and code at the early stages of the SDLC. By harnessing advanced SAST and SCA tools, coupled with our in-depth code and design review skills, we assist clients in detecting security risks within their code, setting correct priorities for mitigation, and strategizing the most effective solutions.
In collaboration with our clients, we refine the security review process by correlating DAST findings with SAST results, pinpointing the exact locations of vulnerabilities in the source code. We also support establishing continuous monitoring mechanisms, providing the necessary tools and guidance to ensure ongoing vigilance and a secure code environment.
Application Security is a Continuous Effort
Since software mistakes cause more than 75% of reported security incidents, applications should be designed, developed, tested, and deployed with security in mind, following the security-by-design paradigm. Application security is a constant process where all stakeholders must be involved – from the business CIO to the last developer – to ensure software quality and integrity.
In this effort, SAST and DAST are essential ingredients of a business’s AppSec arsenal. These complementary tools provide organizations with a powerful arsenal for securing their applications. Coupled with adaptive, secure coding awareness and robust governance, businesses can ensure software and product quality and security, which are essential for maintaining a solid security foundation and protecting sensitive data from the ever-evolving threat landscape.
