AppSec essentials
through the eyes
of international standards
Introduction:
The digital world is constantly evolving and so is the world of cybersecurity. Every year malware and cybersecurity attacks are getting more complex and sophisticated, resulting in more destruction and damages all around the world. Thus, making the creation of Application Security (AppSec from now on) programs and use of best practices in organization applications vital.
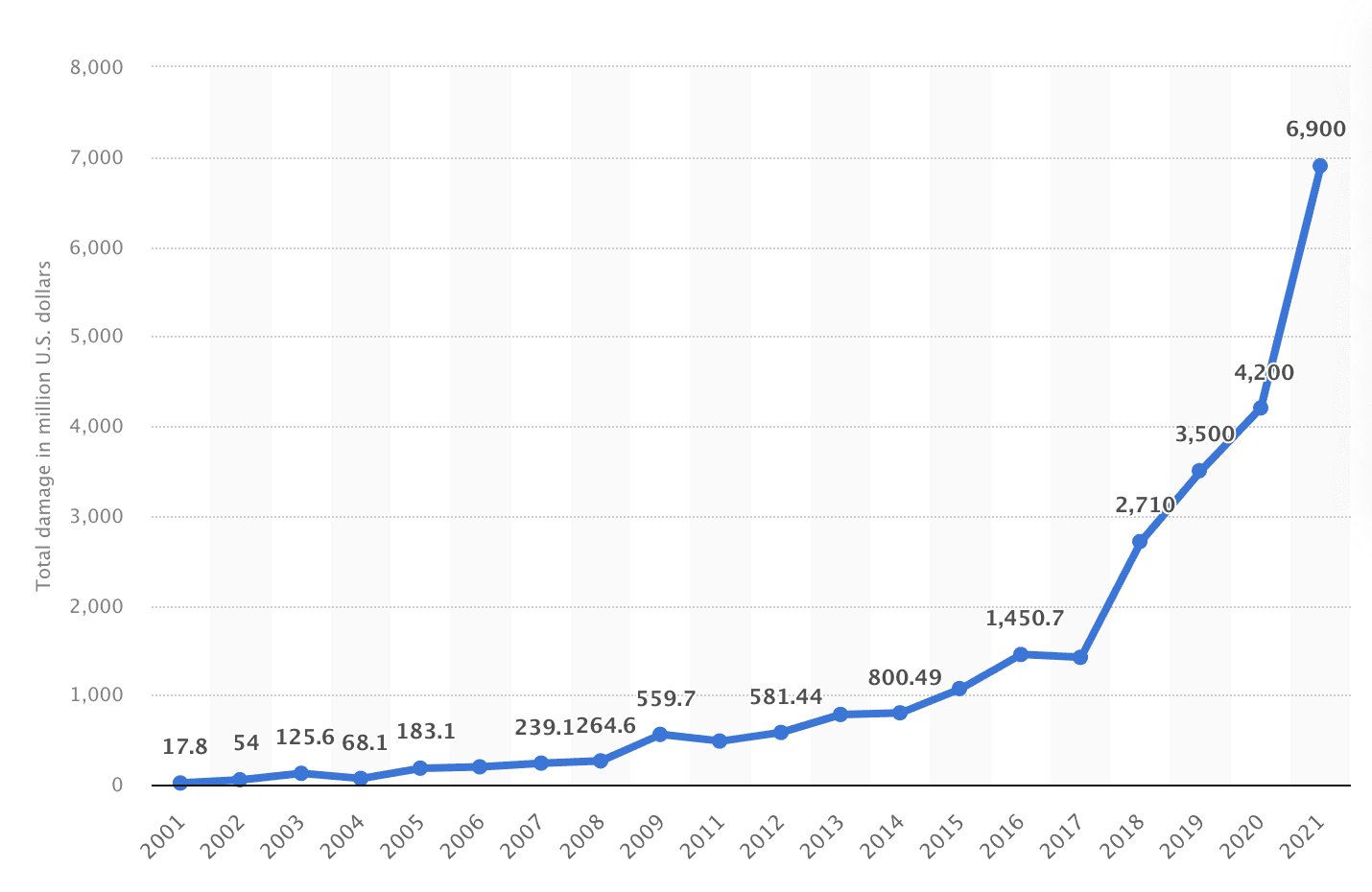
Ransomware is 57x more destructive in 2021 than it was in 2015. Cybercrime cost makes up a value worth 1% of the Global GDP. The global annual cost of cybercrime is estimated to be $6 trillion per year. [1]
In 2021 in the U.S. alone, the cost of cyber crime reported to the Internet Crime Complaint Center (IC3) was 6.9 billion U.S. dollars.
In order to mitigate the risks indicated above, security standards were developed to minimize the volume of security incidents and make applications more secure.
More specifically, there are two international standards that refer to the above:
- PCI DSS which is a security standard that applies to vendors that process credit cardholders’ information [3], and
- “ISO/IEC 27001, which is a certifiable specification for an information security management system and it uses ISO 27002 as a detailed supplementary guide to the security controls in the ISO 27001 framework.” [5]
In this article we are going to talk about what the aforementioned international standards dictate or indicate as essential for an AppSec program within an organization.
Developing and maintaining secure systems and applications
In the following paragraphs we are going to discuss the controls and requirements which refer to AppSec essentials in detail by giving a description of what they refer to, some results and damages from not incorporating them, steps for mitigating the problems that arise and general advice.
1) Secure coding practices
Software development should follow secure coding principles to ensure that applications have security built-in and follow a standard in order to reduce the number of potential security vulnerabilities they contain.
Impact of poor coding practices:
In our practice we usually see that companies follow inadequate coding practices, which results in vulnerabilities, such as use of weak encryption mechanisms and hardcoded credentials in the codebase that can be exploited by malicious actors.
References:
ISO 27002 Control 8.28 – Secure Coding [4]
PCI DSS REQUIREMENT 6 [3]
Steps for mitigation:
- Establishment of secure coding guidelines in a clear and easy to understand format for the developers.
- Strict adherence to those guidelines through use of SAST tools, which enforce coding rules and try to identify known vulnerable patterns like for example, the use of certain functions like strcpy in C.
- Use of IDE SAST tools like eslint and its security plugins, such as eslint-plugin-security.
2) Configuration management
Configurations, including security configurations, of hardware, software, services and networks should be established, documented, implemented, monitored and reviewed in order to avoid alterations by
unauthorized or incorrect changes. Also, open source components/libraries of software systems should be updated regularly to prevent any exploitation of the risks from the use of deprecated versions. From our experience, we have seen a lot of situations where the components/libraries used were never updated or checked for new updates meaning that the vulnerabilities they contain can be areas of weakness for a system’s security.
Impact of outdated software and components:
To stress how important it is to keep everything up to date and use modern technologies we only need to look up the Marriott International incident where the use of outdated technologies resulted in the exposure of half a million of Marriott division Starwood’s guests sensitive data [2].
References:
ISO 27002 Control 8.9 Configuration management [4]
Steps for mitigation:
- Use of SCA(Software Composition Analysis) tools to manage and analyze the open source elements of an application.
- Establishment of procedure for periodical updates and reviews of systems and configurations according to industry best practices.
- Creation of plan for phasing out of outdated and unmaintained software and hardware and replacement by new more efficient and reliable counterparts.
3) Logging and monitoring
Event logs recording user activities, exceptions, faults and information security events should be produced, kept and regularly reviewed. Logging and monitoring mechanisms form an important layer in every organization’s layered defense thanks to the valuable information they present from an investigational, monitoring and troubleshooting aspect. Event logs of all types contain sensitive and important information making it crucial that procedures and mechanisms are set in place to prevent unauthorized access and sensitive data leakage.
Impact of logging and monitoring failures:
The absence of logging or monitoring mechanisms in an application makes it nearly impossible for developers to find a root cause of a performance issue or for incident responders to figure out why a certain event has happened. This results in bigger downtimes and slower identification of breaches or security incidents thereby giving malicious attackers longer time periods to extract sensitive data and cause damage.
References:
ISO 27002 Control 12.4 Logging and monitoring [4]
PCI DSS REQUIREMENT 10[3]
Steps for mitigation:
- Establishment of logging and monitoring mechanisms through the use of industry standard tools and libraries.
- Establishment of processes to secure that no unauthorized party has access to log and monitor data.
- Use of those data to detect and identify possible anomalies in the usage of a network or application.
4) Cryptography
By ensuring that industry accepted cryptographic standards are used in applications and networks, organizations can rest assured that the information and communication is guarded from unauthorized actors and access of information is restricted. Also, through the use of cryptographic techniques, such as MAC (Message Authentication Code) and digital signatures organizations can protect information against spoofing and forgeries thereby ensuring the integrity of information.
Impact of using weak cryptographic algorithms:
- Cases where malicious actors can return encrypted data in its original form and obtain sensitive information.
References:
ISO 27002 Control 10[4]
Steps to mitigate:
- Use of concept “Encryption in layers”, meaning making attackers go through as many encryption layers as possible.
- Use of longest encryption keys that can be supported.
- Use of modern cryptographic ciphers.
- Ensure strict adherence to cryptographic standards that were set.
5) Technical vulnerability management
Any vulnerability constitutes a weakness for a system and must be dealt effectively and efficiently especially when the risks are considerable. Therefore, a need occurs to establish processes in organizations for identifying and detecting vulnerabilities especially on critical systems or those processing, storing sensitive or classified information.
From our experience, the use of SAST and monitoring tools on applications has helped tremendously in preventing exposure to vulnerabilities in a timely fashion. This result comes from the repetitive nature of the monitoring process and its ability to find vulnerabilities effectively and on time.
Also, an additional benefit of monitoring procedures is that by finding the same technical vulnerabilities over a time period the developer teams can take notice and change the way they write code by following more secure coding practices. An important factor in that, is the continuous feedback of the process which also helps the developers understand the findings better thereby increasing the possibility of them fixing the vulnerabilities.
We are stressing this point because of our experience with developer teams of our clients, where they usually neglect fixing critical errors/issues.
From all the above, we can conclude that the combination of the two is the best way to go on reducing and managing technical vulnerabilities in systems.
Risks of no implementation of Technical vulnerability management:
By not implementing the above, organizational risk accumulation of technical vulnerability findings in the SDLC (Software Development Lifecycle) results in not fixing the vulnerabilities due to deadlines on more important features and underfunding. Also, without monitoring or use of code reviews, organizations can’t find critical vulnerabilities in their application due to BlackBox testing limitations.
References:
ISO 27002 Control 12.6 Technical vulnerability management[4]
PCI DSS REQUIREMENT 11[3]
Steps to mitigate:
- Use of SAST and DAST tools combined.
- Regular reviewing of code.
- Establishment of processes for patching of vulnerability findings.
Key takeaways:
- Regular security testing and monitoring of software applications goes a long way in preventing vulnerabilities showing up in later stages of development.
- Organizations need to make sure to keep everything up to date, from the software to the cryptography they use due to the constantly evolving cybersecurity world.
- Applications’ logging and monitoring play a really important role in organizations because of the legal basis they can give if an incident occurs and also from an investigative aspect they give a real good insight to incident responders.
- Secure coding is a concept that is here to stay and organizations need to invest more on it, so that more vulnerabilities are prevented in the early phases of development through the adherence to secure coding best practices.
- Penetration tests or the use of DAST tools is not a complete way of testing an application for security vulnerabilities, due to its blackbox setting. They ignore a whole side of security which can only be covered through whitebox testing. This side refers to business logic issues and vulnerabilities that can be inherited from open source elements of an application, review of implementation of Authentication and Authorization mechanisms or possible sensitive data leakage from logs and issues covered only through code reviews.
References: